欢迎您访问我爱IT技术网,今天小编为你分享的电脑教程是网络协议方面的经验知识教程:基础ACL基本实验,下面是详细的分享!
基础ACL基本实验
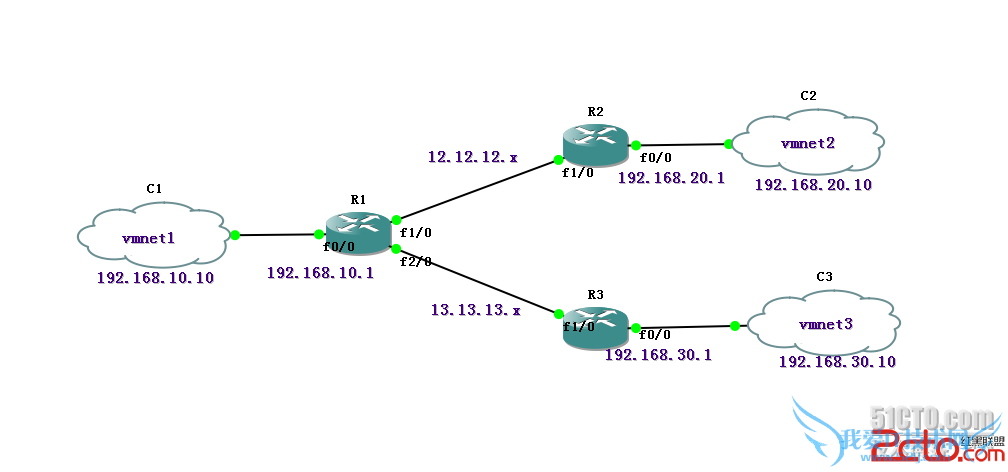
setp 1 基本配置
r1(config)#int fa0/0
r1(config-if)#ip add 192.168.10.1 255.255.255.0
r1(config-if)#no sh
r1(config-if)#int fa1/0
r1(config-if)#ip add 12.12.12.1 255.255.255.0
r1(config-if)#no sh
r1(config-if)#int fa2/0
r1(config-if)#ip add 13.13.13.1 255.255.255.0
r1(config-if)#no sh
r1(config-if)#exit
r1(config)#router ospf 100
r1(config-router)#router-id 1.1.1.1
r1(config-router)#net 0.0.0.0 255.255.255.255 a 0
r1(config-router)#exit
r2(config)#int fa1/0
r2(config-if)#ip add 12.12.12.2 255.255.255.0
r2(config-if)#no sh
r2(config-if)#int fa0/0
r2(config-if)#ip add 192.168.20.1 255.255.255.0
r2(config-if)#no sh
r2(config-if)#exit
r2(config)#router ospf 100
r2(config-router)#router-id 2.2.2.2
r2(config-router)#net 0.0.0.0 255.255.255.255 a 0
r2(config-router)#exit
r3(config)#int fa1/0
r3(config-if)#ip add 13.13.13.3 255.255.255.0
r3(config-if)#no sh
r3(config-if)#exit
r3(config)#int fa0/0
r3(config-if)#ip add 192.168.30.1 255.255.255.0
r3(config-if)#no sh
r3(config-if)#exit
r3(config)#router ospf 100
r3(config-router)#router-id 3.3.3.3
r3(config-router)#net 0.0.0.0 255.255.255.255 area 0
r3(config-router)#exit
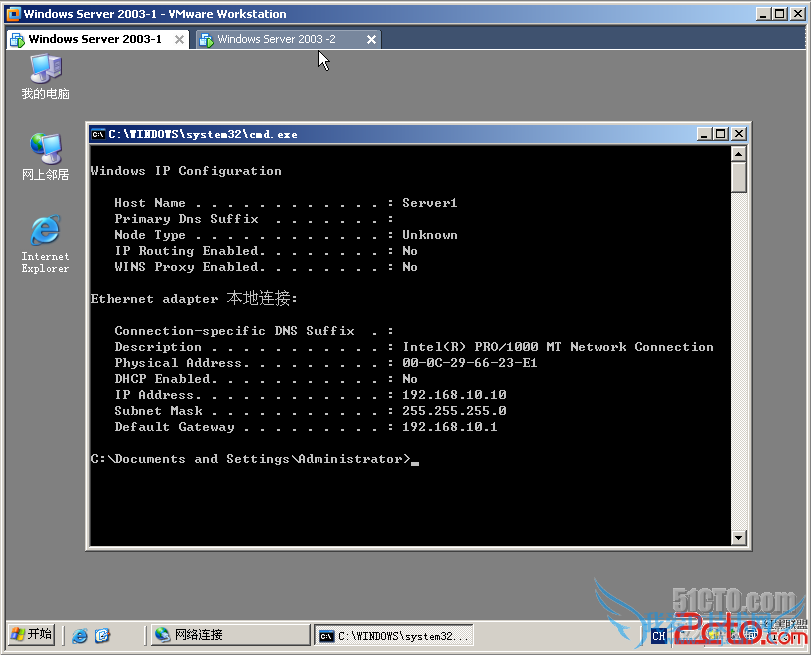
PC1
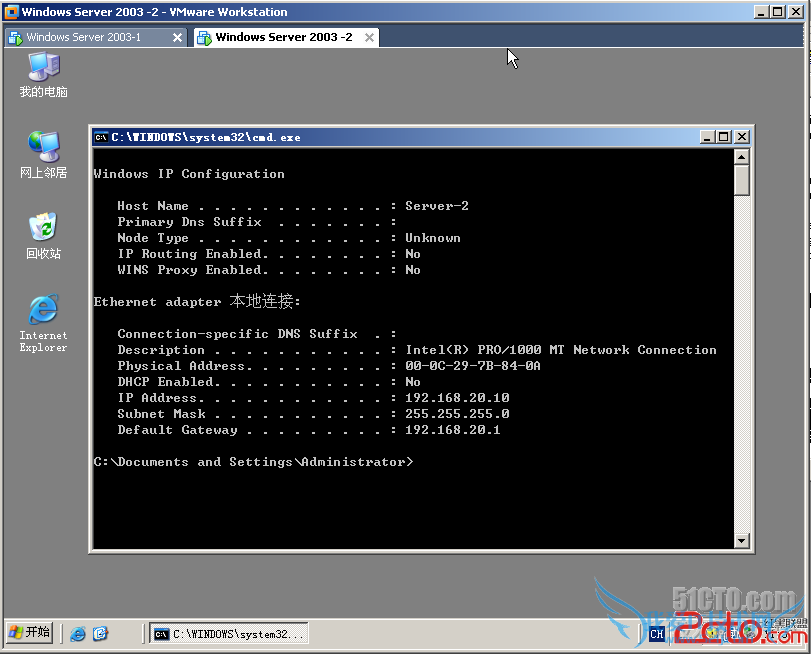
PC2
setp 2 实验
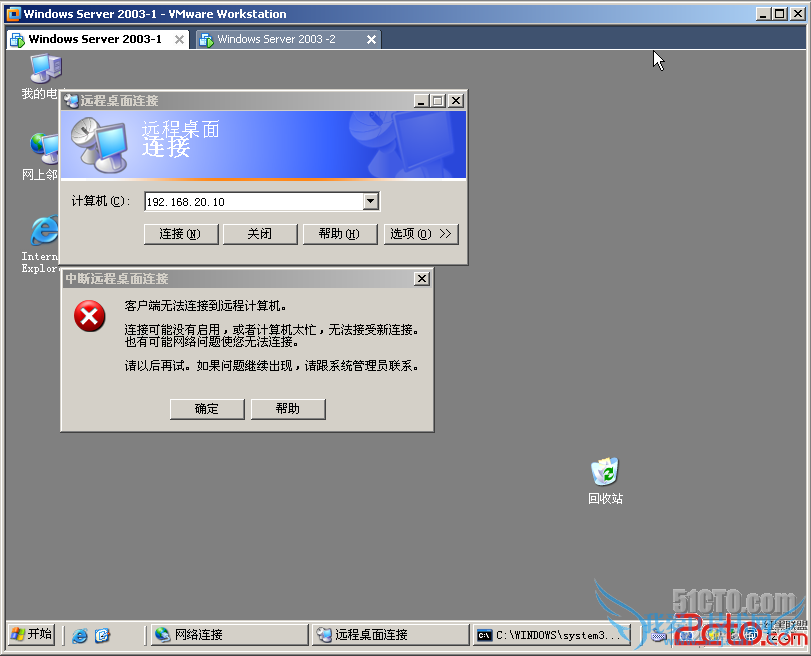
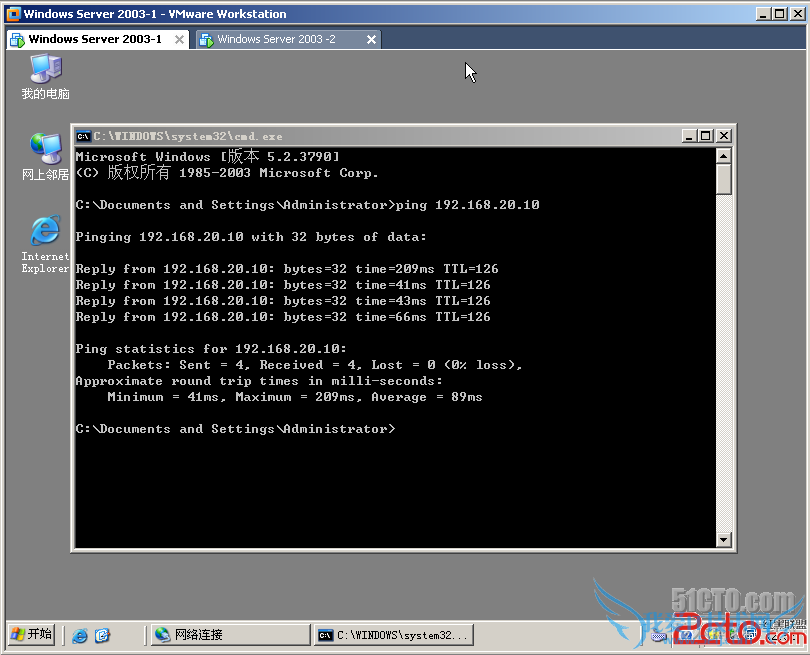
1.PC1不能远程桌面到PC2.可以ping通及telnet
r2(config)#ip access-list extended 100
r2(config-ext-nacl)#deny tcp host 192.168.10.10 host 192.168.20.10 eq 3389
r2(config-ext-nacl)#permit ip any any
r2(config)#int fa1/0
r2(config-if)#ip acce
r2(config-if)#ip access-group 100 in
r2(config-if)#exit
r2(config)#exit
r2#show ip access-lists
Extended IP access list 100
10 deny tcp host 192.168.10.10 host 192.168.20.10 eq 3389 (6 matches)
20 permit ip any any (8 matches)
2.要求:只允许PC1中IP地址为偶数的能ping通PC2
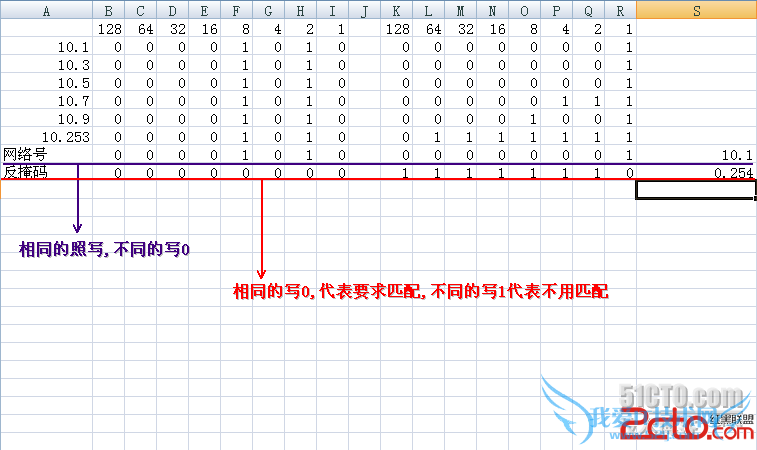
r2(config)#ip access-list extended 101
r2(config-ext-nacl)#deny ip 192.168.10.1 0.0.0.254 host 192.168.20.10
r2(config-ext-nacl)#permit ip any any
r2(config)#int fa1/0
r2(config-if)#ip access-group 101 in
r2(config-if)#no sh
r2(config-if)#exit
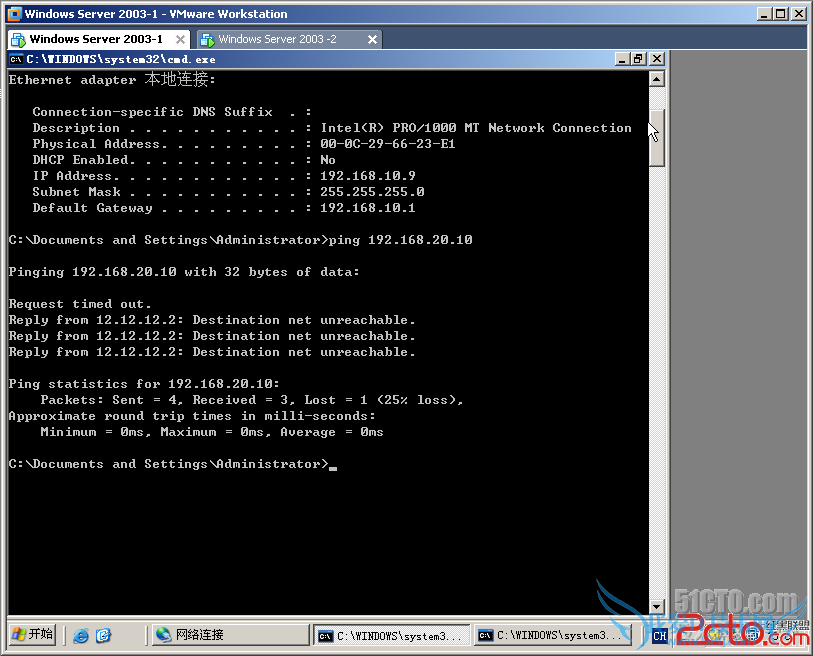
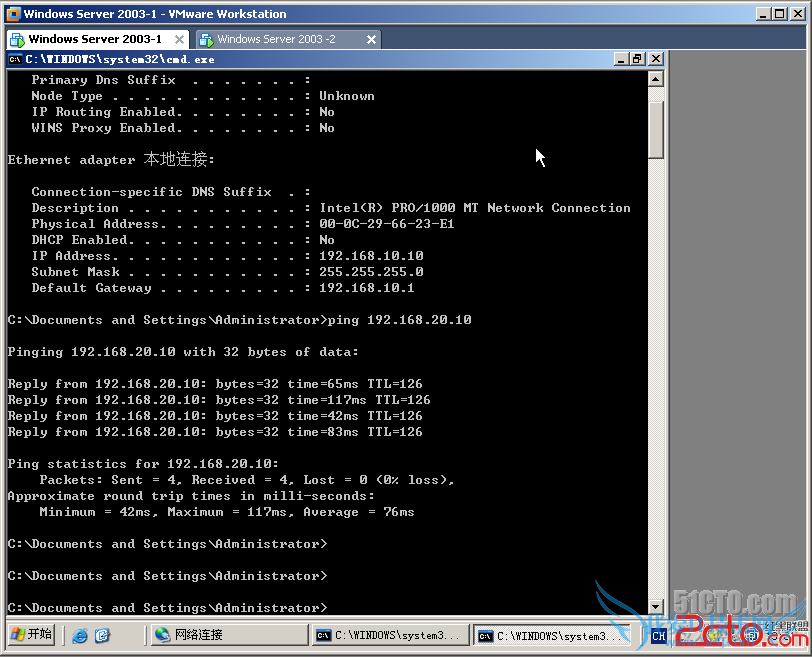
r2#show ip access-lists
Extended IP access list 101
10 deny ip 192.168.10.1 0.0.0.254 host 192.168.20.10 (12 matches)
20 permit ip any any (54 matches)
3. ACL错误写法
r2(config)#ip access-list extended 100
r2(config)#deny ip 192.168.10.10 255.255.255.255 192.168.20.10 255.255.255.255 //转换成any 到any了
r2(config-ext-nacl)#exit
r2#show ip access-lists
Extended IP access list 100
10 deny ip any any
4.ACL标准写法
deny PC1 192.168.10.10 ---->192.168.20.10
r1(config)#access-list 1 deny host 192.168.10.10
r1(config)#access-list 1 permit any
r1(config)#int fa0/0
r1(config-if)#ip access-group 1 in
r1(config)#exit
r1#show ip access-lists
Standard IP access list 1
10 deny 192.168.10.10 (12 matches)
20 permit any (64 matches)
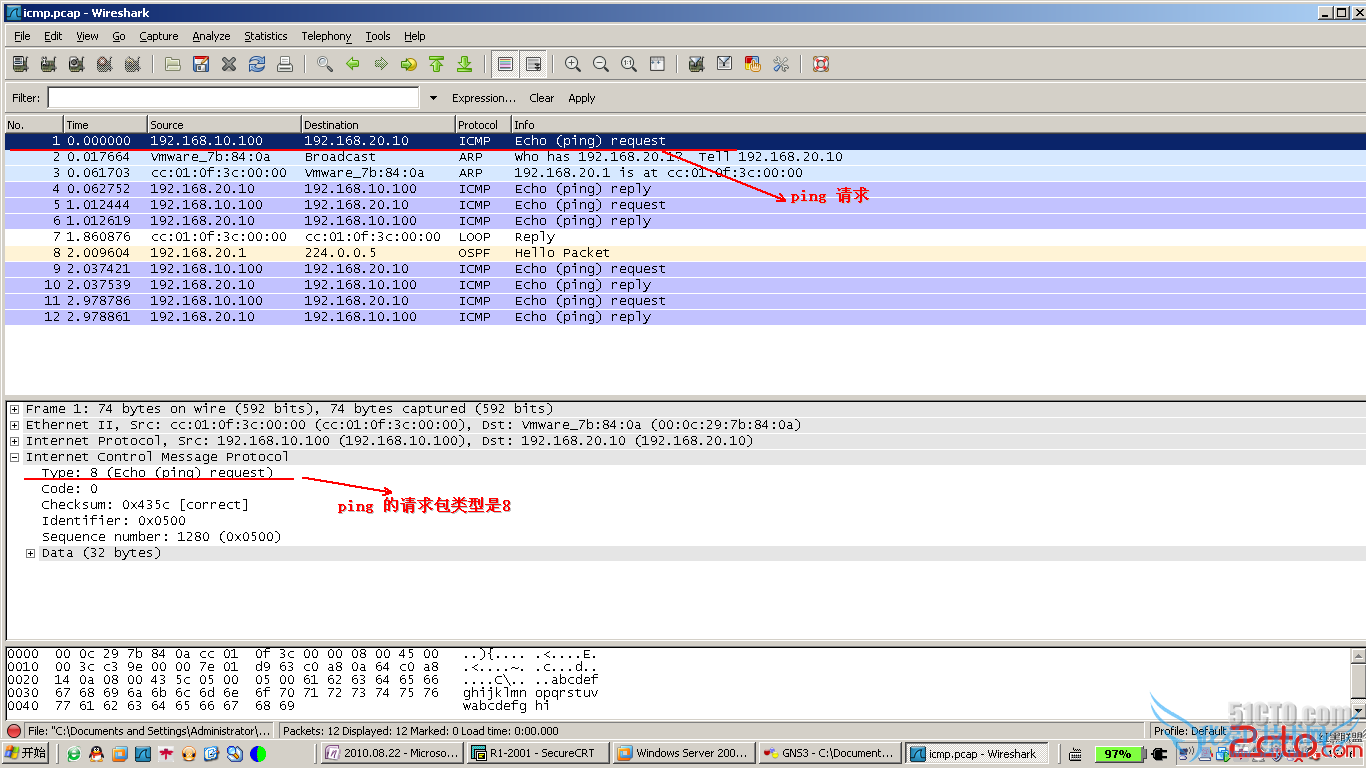
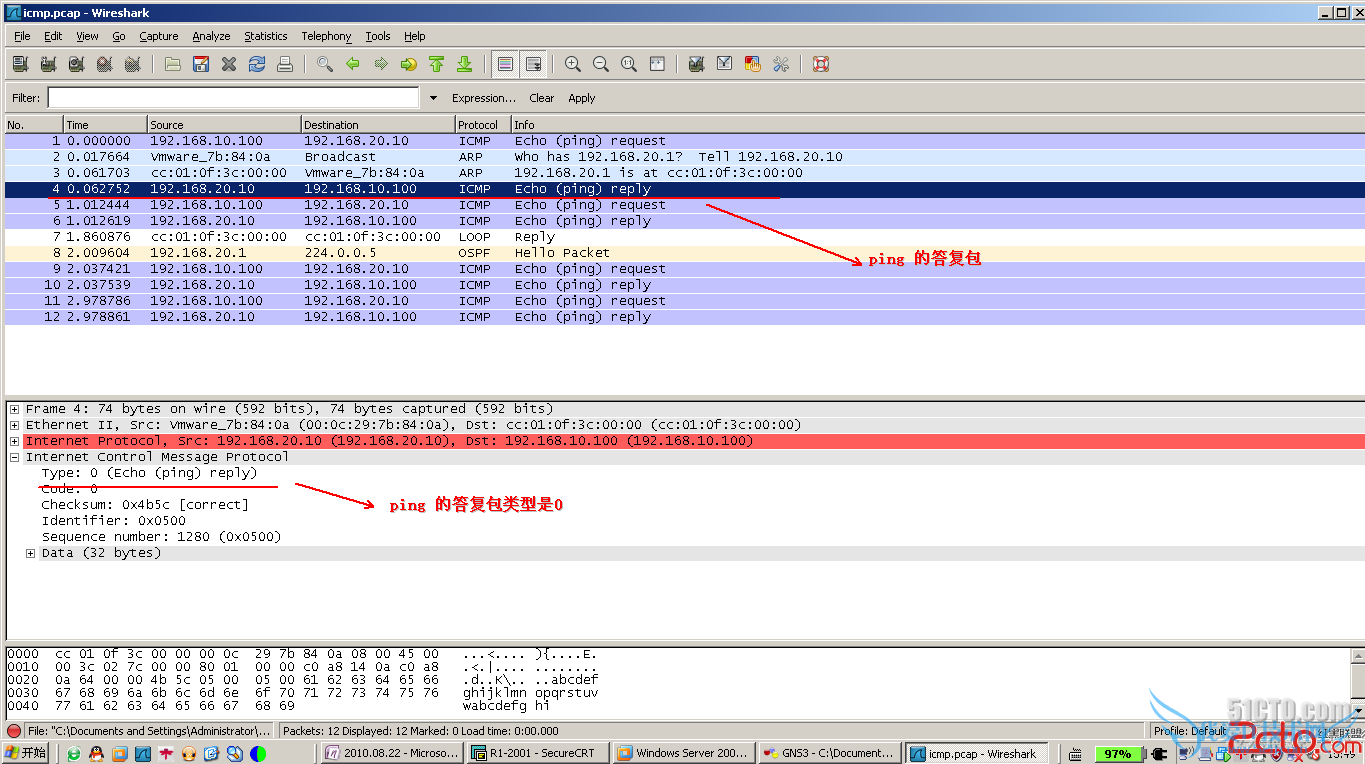
5. ACL扩展写法
要求192.168.10.0网段不能远程桌面到192.168.20.10,可以ping及telnet
r1(config)#access-list 101 deny tcp 192.168.10.0 0.0.0.255 host 192.168.20.10eq 3389
r1(config)#access-list 101 permit ip any any
r1(config)#int fa0/0
r1(config-if)#ip access-group 101 in
r1(config-if)#exit
r1#show ip access-lists
Extended IP access list 101
10 deny tcp 192.168.10.0 0.0.0.255 host 192.168.20.10 eq 3389 (9 matches)
20 permit ip any any (39 matches)
6. 命名ACL
好处:可以对单独的某一条语句进行修改
r1(config)#ip access-list extended a
r1(config-ext-nacl)#deny tcp 192.168.10.0 0.0.0.255 host 192.168.20.10 eq 3389
r1(config-ext-nacl)#permit ip any any
r1(config-ext-nacl)#int fa0/0
r1(config-if)#ip access-group a in
r1(config)#ip access-list extended a
r1(config-ext-nacl)#15 deny tcp 192.168.10.0 0.0.0.255 host 192.168.20.10 eqtelnet
r1(config-ext-nacl)#do show ip access
Extended IP access list a
10 deny tcp 192.168.10.0 0.0.0.255 host 192.168.20.10 eq 3389 (63 matches)
15 deny tcp 192.168.10.0 0.0.0.255 host 192.168.20.10 eq telnet (6 matches)
20 permit ip any any (125 matches)
7. ICMP的ACL
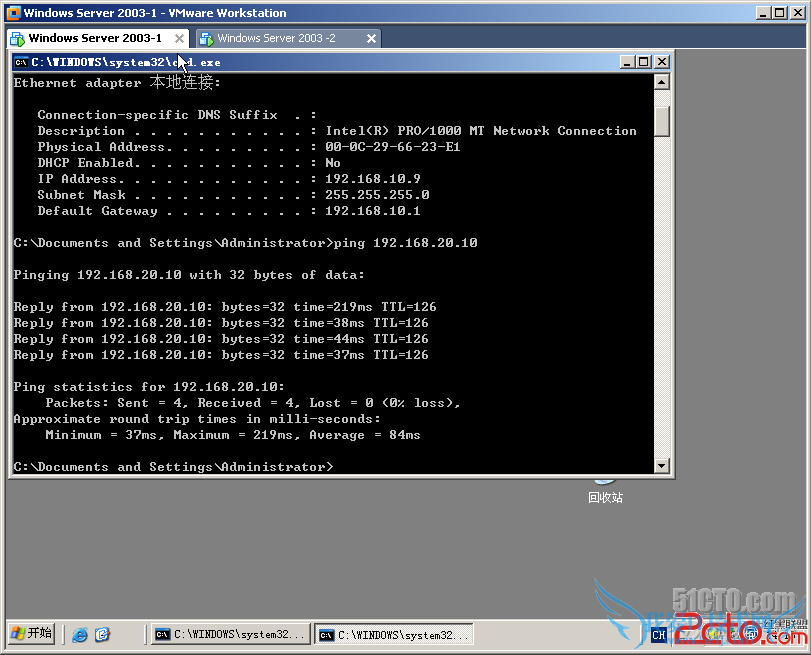
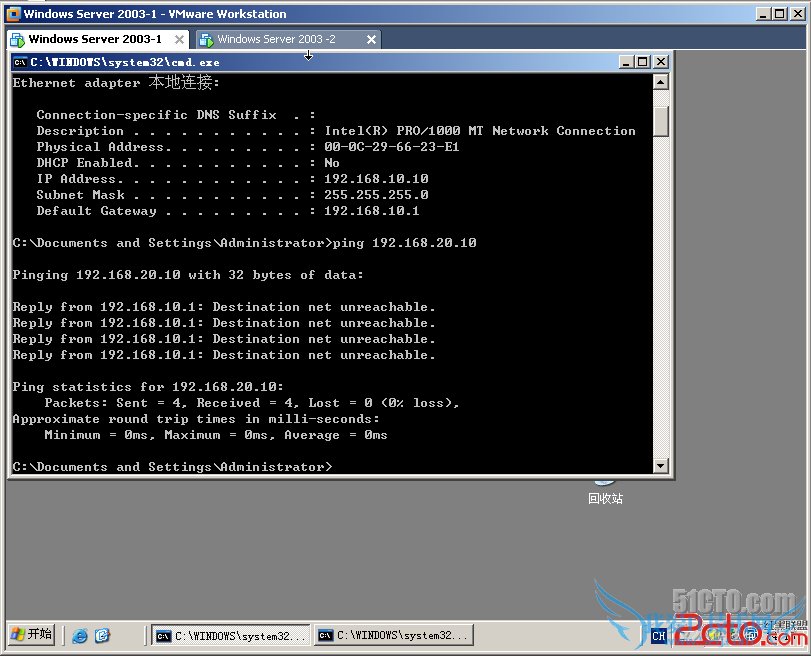
要求: 192.168.10.10 不能ping 192.168.20.10,而192.168.20.10能ping 192.168.10.10
8. ACL 对自己出包不起作用
在R2上做ACL,使R2不能对R1telnet
r2#telnet 12.12.12.1
Trying 12.12.12.1 ... Open
User Access Verification
Password:
r1>exit
[Connection to 12.12.12.1 closed by foreign host]
r2(config)#access-list 100 deny tcp host 12.12.12.1 eq 23 host 12.12.12.2
r2(config)#access-list 100 permit ip any any
r2(config)#int fa1/0
r2(config-if)#ip access-group 100 in
r2(config-if)#no sh
r2(config-if)#exit
r2(config)#exit
r2#show ip access-lists 100
Extended IP access list 100
10 deny tcp host 12.12.12.1 eq telnet host 12.12.12.2
20 permit ip any any (2 matches)
r2#telnet 12.12.12.1
Trying 12.12.12.1 ...
% Connection timed out; remote host not responding
r2#show ip access-lists
Extended IP access list 100
10 deny tcp host 12.12.12.1 eq telnet host 12.12.12.2 (12 matches)
20 permit ip any any (7 matches)
9. VTY 应用ACL
r1(config)#access-list 10 per
r1(config)#access-list 10 permit 192.168.20.10 //只允许192.168.20.10对此设备telnet
r1(config)#line vty 0 4
r1(config-line)#acc
r1(config-line)#access-class 10 in
r1(config-line)#exit
以上就是关于基础ACL基本实验的网络协议知识分享,更多电脑教程请移步到>>电脑教程。
- 评论列表(网友评论仅供网友表达个人看法,并不表明本站同意其观点或证实其描述)
-
