欢迎您访问我爱IT技术网,今天小编为你分享的电脑教程是网络协议方面的经验知识教程:ASA5510与ASA5505(PPPOE获取地址)EzVPN配置,下面是详细的分享!
ASA5510与ASA5505(PPPOE获取地址)EzVPN配置
ASA5510与ASA5505(PPPOE获取地址)EzVPN配置
一:拓撲
![clip_image002[4]](http://www.52ij.com/uploads/allimg/160228/1319552K8-0.jpg)
本次试验的主要目标是展示三个重要的知识点
1.ASA5505如何配置EzVPN硬件客户端(注意ASA5510及其以上只能配置成为EzVPN服务器)。
2.ASA如何配置PPPOE客户端。
3.ASA5510上配置EzVPN网络扩展模式,一个容易被忽视的配置点。
二:需求
1. ASA5505通過PPPOE撥號訪問互聯網,並且保證內部網絡可以訪問互聯網
2. ASA5505作為EzVPN的硬件客戶端,ASA5510作为的EzVPN服务器
3. ASA5510要保證內部網絡可以訪問互聯網
4. 確定,ASA5505.Inside和ASA5510.Inside之間可以通過EzVPN互訪
三:配置
1. ASA5505.Inside
ASA5505.Inside#sh run
Building configuration...
Current configuration : 648 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname ASA5505.Inside
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
ip cef
!
!
!
!
no ip domain lookup
!
multilink bundle-name authenticated
!
!
!
!
!
archive
log config
hidekeys
!
!
!
!
!
!
!
interface FastEthernet0
ip address 192.168.1.1 255.255.255.0
speed auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 192.168.1.10
!
!
no ip http server
no ip http secure-server
!
!
!
!
control-plane
!
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
password cisco
login
!
end
2. ASA5505
ASA5505(config)# sh run
: Saved
:
ASA Version 8.0(5)
!
hostname ASA5505
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Vlan30
nameif outside
security-level 0
pppoe client vpdn group pppoe
ip address pppoe setroute
!
interface Vlan40
nameif inside
security-level 100
ip address 192.168.1.10 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 30
!
interface Ethernet0/1
switchport access vlan 40
!
interface Ethernet0/2
shutdown
!
interface Ethernet0/3
shutdown
!
interface Ethernet0/4
shutdown
!
interface Ethernet0/5
shutdown
!
interface Ethernet0/6
shutdown
!
interface Ethernet0/7
shutdown
!
ftp mode passive
access-list out extended permit icmp any any
access-list bypass extended permit ip 192.168.1.0 255.255.255.0 172.16.1.0 255.255.255.0
pager lines 24
mtu outside 1500
mtu inside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 1 192.168.1.0 255.255.255.0
access-group out in interface outside
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
telnet timeout 5
ssh timeout 5
console timeout 0
vpdn group pppoe request dialout pppoe
vpdn group pppoe localname pppoeuser1
vpdn group pppoe ppp authentication pap
vpdn username pppoeuser1 password *********
vpnclient server 64.102.51.10
vpnclient mode network-extension-mode
vpnclient nem-st-autoconnect
vpnclient vpngroup yeslab password ********
vpnclient username testuser1 password ********
vpnclient enable
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:947bd7e354635e160ddb59a18b6d59e3
: end
3.PPPOE.Server
PPPOE.Server#sh run
Building configuration...
Current configuration : 1064 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname PPPOE.Server
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
ip cef
!
!
!
!
no ip domain lookup
!
multilink bundle-name authenticated
vpdn enable
!
!
!
!
!
!
username pppoeuser1 password 0 cisco
archive
log config
hidekeys
!
!
!
!
!
!
bba-group pppoe global
virtual-template 1
!
!
interface FastEthernet0
no ip address
speed auto
!
interface FastEthernet0.10
encapsulation dot1Q 10
ip address 202.100.1.1 255.255.255.0
!
interface FastEthernet0.30
encapsulation dot1Q 30
pppoe enable group global
!
interface Virtual-Template1
ip unnumbered FastEthernet0.10
peer default ip address pool ippool
ppp authentication pap
!
ip local pool ippool 202.100.1.100 202.100.1.200
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 202.100.1.254
!
!
no ip http server
no ip http secure-server
!
!
!
!
control-plane
!
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
password cisco
login
!
end
4. INTERNET
Internet#sh run
Building configuration...
Current configuration : 788 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Internet
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 25
ip cef
!
!
!
!
no ip domain lookup
!
multilink bundle-name authenticated
!
!
!
!
!
archive
log config
hidekeys
!
!
!
!
!
!
!
interface FastEthernet0
no ip address
speed auto
!
interface FastEthernet0.10
encapsulation dot1Q 10
ip address 202.100.1.254 255.255.255.0
!
interface FastEthernet0.20
encapsulation dot1Q 20
ip address 64.102.51.254 255.255.255.0
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
!
!
!
!
control-plane
!
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
password cisco
login
!
end
5. ASA5510
ASA5510(config)# sh run
: Saved
:
ASA Version 8.0(2)
!
hostname ASA5510
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 64.102.51.10 255.255.255.0
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 172.16.1.10 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/5
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list out extended permit icmp any any
access-list split extended permit ip 172.16.1.0 255.255.255.0 any
access-list bypass extended permit ip 172.16.1.0 255.255.255.0 192.168.1.0 255.255.255.0
pager lines 24
mtu outside 1500
mtu inside 1500
ip local pool ezpool 123.1.1.100-123.1.1.200
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list bypass
nat (inside) 1 0.0.0.0 0.0.0.0
access-group out in interface outside
route outside 0.0.0.0 0.0.0.0 64.102.51.254 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set cisco esp-des esp-md5-hmac
crypto dynamic-map dymap 100 set transform-set cisco
crypto dynamic-map dymap 100 set reverse-route
crypto map cisco 10 ipsec-isakmp dynamic dymap
crypto map cisco interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
crypto isakmp policy 65535
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
group-policy yeslabccies internal
group-policy yeslabccies attributes
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split
nem enable
username testuser1 password i1lji/GiOWB67bAs encrypted
username testuser1 attributes
vpn-group-policy yeslabccies
tunnel-group yeslab type remote-access
tunnel-group yeslab general-attributes
address-pool ezpool
tunnel-group yeslab ipsec-attributes
pre-shared-key *
prompt hostname context
Cryptochecksum:edd654a1ddf97d90c02f2f55d1e9a09e
: end
6. ASA5510.Inside
ASA5510.Inside#sh run
Building configuration...
Current configuration : 727 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname ASA5510.Inside
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 15
ip cef
!
!
!
!
no ip domain lookup
!
multilink bundle-name authenticated
!
!
!
!
!
archive
log config
hidekeys
!
!
!
!
!
!
!
interface Ethernet0
no ip address
shutdown
half-duplex
!
interface FastEthernet0
ip address 172.16.1.1 255.255.255.0
speed auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 172.16.1.10
!
!
no ip http server
no ip http secure-server
!
!
!
!
control-plane
!
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
password cisco
login
!
end
四:測試
1. ASA5505通過PPPOE.Server獲得IP地址:
![clip_image004[4]](http://www.52ij.com/uploads/allimg/160228/1319554962-1.jpg)
2. ASA5505.Inside測試上網:
![clip_image006[4]](http://www.52ij.com/uploads/allimg/160228/131955B17-2.jpg)
3. ASA5505作為EzVPN硬件客戶端的狀態:
![clip_image008[4]](http://www.52ij.com/uploads/allimg/160228/13195560V-3.jpg)
4. ASA5505設備上展示ISAKMP SA 和IPSEC SA:
![clip_image010[4]](http://www.52ij.com/uploads/allimg/160228/1319552245-4.jpg)
![clip_image012[4]](http://www.52ij.com/uploads/allimg/160228/1319554459-5.jpg)
5. ASA5510.Inside測試上網:
![clip_image014[4]](http://www.52ij.com/uploads/allimg/160228/1319551238-6.jpg)
6. ASA5510設備上展示ISAKMP SA和IPSEC SA:
![clip_image016[4]](http://www.52ij.com/uploads/allimg/160228/131955CP-7.jpg)
![clip_image018[4]](http://www.52ij.com/uploads/allimg/160228/13195539A-8.jpg)
7. ASA5505.Inside和ASA5510.Inside之間互訪:
![clip_image020[4]](http://www.52ij.com/uploads/allimg/160228/1319555928-9.jpg)
![clip_image022[4]](http://www.52ij.com/uploads/allimg/160228/1319555336-10.jpg)
五:注意
1. 在ASA5505上系統會自動添加一個BYPASS掉EzVPN感興趣流流量的ACL
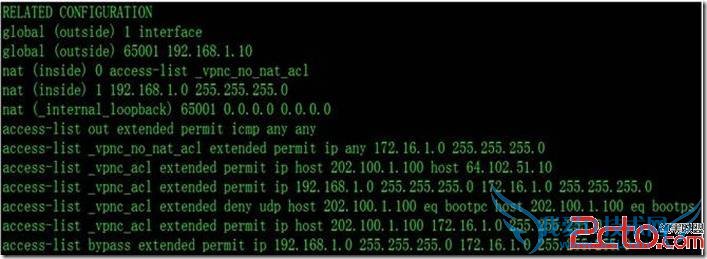
以上就是关于ASA5510与ASA5505(PPPOE获取地址)EzVPN配置的网络协议知识分享,更多电脑教程请移步到>>电脑教程。
- 评论列表(网友评论仅供网友表达个人看法,并不表明本站同意其观点或证实其描述)
-
