欢迎您访问我爱IT技术网,今天小编为你分享的电脑教程是网络协议方面的经验知识教程:H3C MSR 3016与Cisco 5510 ipsec vpn互联,下面是详细的分享!
H3C MSR 3016与Cisco 5510 ipsec vpn互联
H3C MSR 3016与Cisco 5510 ipsec vpn互联
前言:
书接上文 http:///net/201210/162034.html ,之前分部的一个VPN(cisco5510)设备损坏,临时找来一台备用的VPN(H3C Msr3016),刷完系统后,开始设置IPSEC VPN,幸好之前备份过CISCO5510的配置,按照原来的配置重新配置H3C msr 3016。
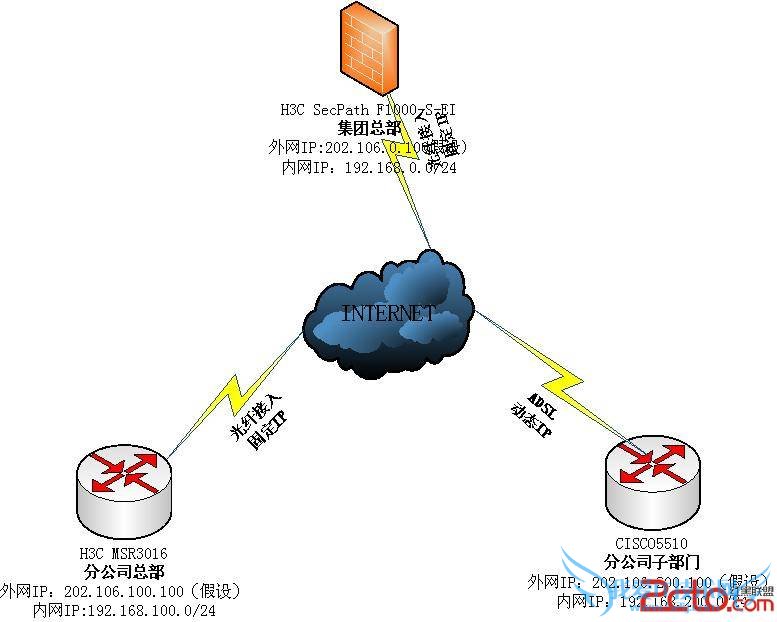
这是总体的网络拓扑图,此文章中着重讲解h3c msr3016(固定IP)与Cisco 5510(动态ip)之间的IPSEC VPN 建立。
先上H3C MSR 3016(分公司总部)的配置:
(省略无关部分)
[ruby]
version 5.20, Release 2207P02, Basic
acl number 3000
rule 0 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.0.0 0.0.0.255 (分公司总部到集团总部的数据流)
acl number 3010 name denynat
rule 1 deny ip source 192.168.100.0 0.0.0.255 destination 192.168.0.0 0.0.0.255 (nat 数据流 这里是指定去往集团总部的数据流不被nat)
rule 2 deny ip source 192.168.100.0 0.0.0.255 destination 192.168.200.0 0.0.0.255(nat 数据流 这里是指定去往分公司子部门的数据流不被nat)
acl number 3030
rule 0 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.200.0 0.0.0.255(分公司总部到分公司子部门的数据流)
#
ike proposal 10 (ike安全提议 使用默认的与集团的H3C互联)
#
ike proposal 20
authentication-algorithm md5 (ike安全提议 与分公司子部门的Cisco互联)
#
ike peer jtuanzongbu ike 对等体名称 (匹配集团总部)
exchange-mode aggressive (野蛮模式)
pre-shared-key cipher n3MZ9hvCSV3O1hkSNpRHtg== 共享密钥
id-type name
remote-name jtzongbu
remote-address 202.106.0.100
local-address 202.106.100.100
nat traversal (nat穿透)
#
ike peer fenbu ike 对等体名称 (匹配分公司子部门)
exchange-mode aggressive
pre-shared-key simple 000000
id-type name
remote-name Fenbu1 (Cisco 设备名称)因为对方Cisco5510为动态IP地址 这里指定名称
local-address 202.106.100.100
#
ipsec proposal 10 ipsec 安全提议
#
ipsec policy branch 10 isakmp (设置ipsec policy 名称 子号码 这里是10、20)
security acl 3000
pfs dh-group1
ike-peer jtzongbu
proposal 10
#
ipsec policy branch 20 isakmp
security acl 3030
pfs dh-group1
ike-peer fenbu
proposal 10
#
interface Ethernet0/0
port link-mode route
description outside
nat outbound 3010
ip address 202.106.100.100 255.255.255.248
ipsec policy branch 在外网接口应用此策略
#
interface Ethernet0/1
port link-mode route
description inside
ip address 192.168.100.1 255.255.255.0
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 202.106.100.101 设置默认路由
Cisco5510 (分公司子部门)配置:
[ruby]
Fenbu1# show configuration
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.200.1 255.255.255.0
!
interface Management0/0
nameif management
security-level 100
ip address 192.168.50.1 255.255.255.0
management-only
!
boot system disk0:/asa831-k8.bin
ftp mode passive
dns domain-lookup outside
dns server-group DefaultDNS
name-server 202.96.128.86
object network obj-192.168.200.0 配置网络对象区域,方便后边调用
subnet 192.168.200.0 255.255.255.0
object network obj-192.168.0.0
subnet 192.168.0.0 255.255.255.0
object network obj-192.168.0.0
subnet 192.168.0.0 255.255.255.0
object network obj-192.168.100.0
subnet 192.168.100.0 255.255.0.0
object network obj_any
subnet 0.0.0.0 0.0.0.0
access-list 100 extended permit ip any any 设置ACL表
access-list 200 extended permit ip host 192.168.200.20 any
access-list 200 extended permit ip host 192.168.200.30 any
access-list 102 extended permit ip 192.168.200.0 255.255.255.0 192.168.100.0 255.255.255.0
access-list 103 extended permit ip 192.168.200.0 255.255.255.0 192.168.0.0 255.255.255.0
nat (inside,any) source static obj-192.168.200.0 obj-192.168.200.0 destination static obj-192.168.0.0 obj-192.168.0.0
nat (inside,any) source static obj-192.168.200.0 obj-192.168.200.0 destination static obj-192.168.100.0 obj-192.168.100.0
!
object network obj_any
nat (inside,outside) dynamic interface
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-record DfltAccessPolicy
aaa authentication ssh console LOCAL
aaa authentication http console LOCAL
http server enable
http 192.168.100.0 255.255.255.0 management
http 0.0.0.0 0.0.0.0 outside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set firstset esp-des esp-md5-hmac (ipsec 配置)
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto map mymap 2 match address 103 (创建保密图相当于H3C的ipsec policy)
crypto map mymap 2 set pfs group1
crypto map mymap 2 set peer 202.106.0.100 分公司子部门与集团总部互联
crypto map mymap 2 set transform-set firstset
crypto map mymap 2 set phase1-mode aggressive group1
crypto map mymap 10 match address 102
crypto map mymap 10 set pfs group1
crypto map mymap 10 set peer 202.106.100.100 分公司子部门与分公司总部互联
crypto map mymap 10 set transform-set firstset
crypto map mymap interface outside
crypto isakmp identity address
crypto isakmp enable outside
crypto isakmp policy 1 (ike 配置,配置多个匹配不同的IKE加密)
authentication pre-share
encryption des
hash md5
group 1
lifetime 86400
crypto isakmp policy 20
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp policy 30
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
crypto isakmp nat-traversal 60
tunnel-group DefaultL2LGroup ipsec-attributes
pre-shared-key *****
tunnel-group 202.106.100.100 type ipsec-l2l
tunnel-group 202.106.100.100 ipsec-attributes (分公司总部的共享密钥)
pre-shared-key *****
tunnel-group 202.106.0.100 type ipsec-l2l
tunnel-group 202.106.0.100 ipsec-attributes (集团总部的共享密钥)
pre-shared-key *****
配置完毕!
以上就是关于H3C MSR 3016与Cisco 5510 ipsec vpn互联的网络协议知识分享,更多电脑教程请移步到>>电脑教程。
- 评论列表(网友评论仅供网友表达个人看法,并不表明本站同意其观点或证实其描述)
-
